In today’s interconnected world, robust network security is paramount. The concept of a Demilitarized Zone (DMZ), borrowed from the military, plays a crucial role in safeguarding internal networks.
What is a DMZ?
Just like a demilitarized zone acts as a neutral space between conflicting nations, a network DMZ serves as a buffer zone between your trusted internal network and the untrusted external network (usually the internet). This separation creates an extra layer of security for your critical systems.
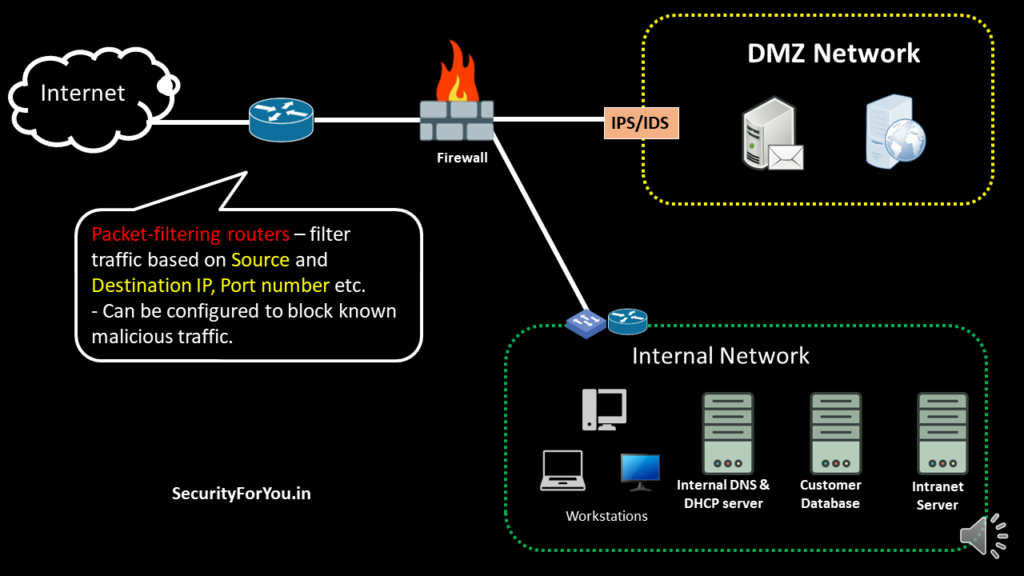
Network Borders and Firewalls: The First Line of Defense
Imagine your internal network as a castle. The network borders, similar to castle walls, function as the first line of defense. Firewalls, like vigilant guards, meticulously filter incoming and outgoing traffic, allowing only authorized requests to pass through. They block unauthorized traffic, preventing outsiders from directly accessing internal systems.
The Role of the DMZ: A Secure Outpost
Certain services, like web servers, email servers, or public-facing applications, reside within the DMZ. This allows external users to access these services without directly interacting with your internal network.
Example: A company website hosted on a web server in the DMZ lets external users browse and interact without compromising internal systems that store sensitive data.
Minimizing Vulnerabilities in the DMZ
Devices within the DMZ are configured to have only the functionalities essential for their designated services. This reduces potential vulnerabilities. For instance, a mail server in the DMZ might only have email-related services enabled, minimizing the attack surface for hackers.
Additional Security Measures in the DMZ
- Intrusion Detection/Prevention Systems (IDS/IPS): These act as vigilant watchdogs within the DMZ, monitoring, recording, and potentially blocking suspicious activities.
- Example: An IDS in the DMZ might detect and log multiple failed login attempts on a web server, indicating a potential brute-force attack. It could then alert the network administrator and block the suspicious traffic.
Firewalls: Guardians at the DMZ Gate
Firewalls in the DMZ act as an additional security layer. Positioned behind packet-filtering routers, they pre-screen incoming traffic, blocking obvious threats before they reach the internal network.
- Packet-filtering routers: These act as initial gatekeepers, filtering traffic based on pre-defined criteria like source and destination IP addresses, port numbers, etc. They can block known malicious traffic.
- Firewalls in the DMZ: These ensure incoming traffic from external sources is directed only to the DMZ, where services intended for outside use are located. They meticulously route external requests to the web server, maintaining a controlled flow of traffic.
Protecting Critical Assets: Keeping the Crown Jewels Safe
Critical organizational assets, like the main database containing sensitive customer information, are never placed within the DMZ. They reside securely within the internal network, further shielded from potential attacks.
Benefits of a DMZ:
- Enhanced Security: By not allowing external users direct access to the internal network, a DMZ adds a layer of protection to critical systems. Even if attackers compromise the DMZ, they cannot directly access internal servers.
- Improved Traffic Flow: The DMZ facilitates efficient management of external traffic without impacting internal network performance.
DMZ vs. Extranet: Understanding the Difference
An extranet is a separate network that allows controlled access to specific external users, such as business partners or customers. It functions like an extension of the internal network, granting access to authorized external users to collaborate securely. Unlike a DMZ, which focuses on specific services, an extranet provides access to a wider range of internal resources in a controlled manner.
Conclusion
The DMZ concept, effectively implemented, strengthens your network security posture. By creating a buffer zone and implementing additional security measures, you can safeguard your critical assets and ensure a secure flow of information within your organization.